This room is all about finding ways to pwn the Kioptrix1 machine from VulnHub as part of the preparation for PNPT.
We’re not going to stop at how to setup the machine on Vmware or Virtualbox, that’s an easy task to accomplish. Once set up, there’s couple of methods i use to find the ip address.
1. From the kioptrix machine, ping something - the result will also display the local machine IP.
2. Use "Netdiscover" or "Nmap" on the kali machine to find the hosts on the local network and determine which one is Kioptrix.
As we most of the times do, let’s start scanning with nmap. I recently learned in the Ethical Hacker course from Cisco that using stealth(-sS) scan is actually faster than a default TCP Connect(-sT), as it doesn’t fully complete the 3-way handshake
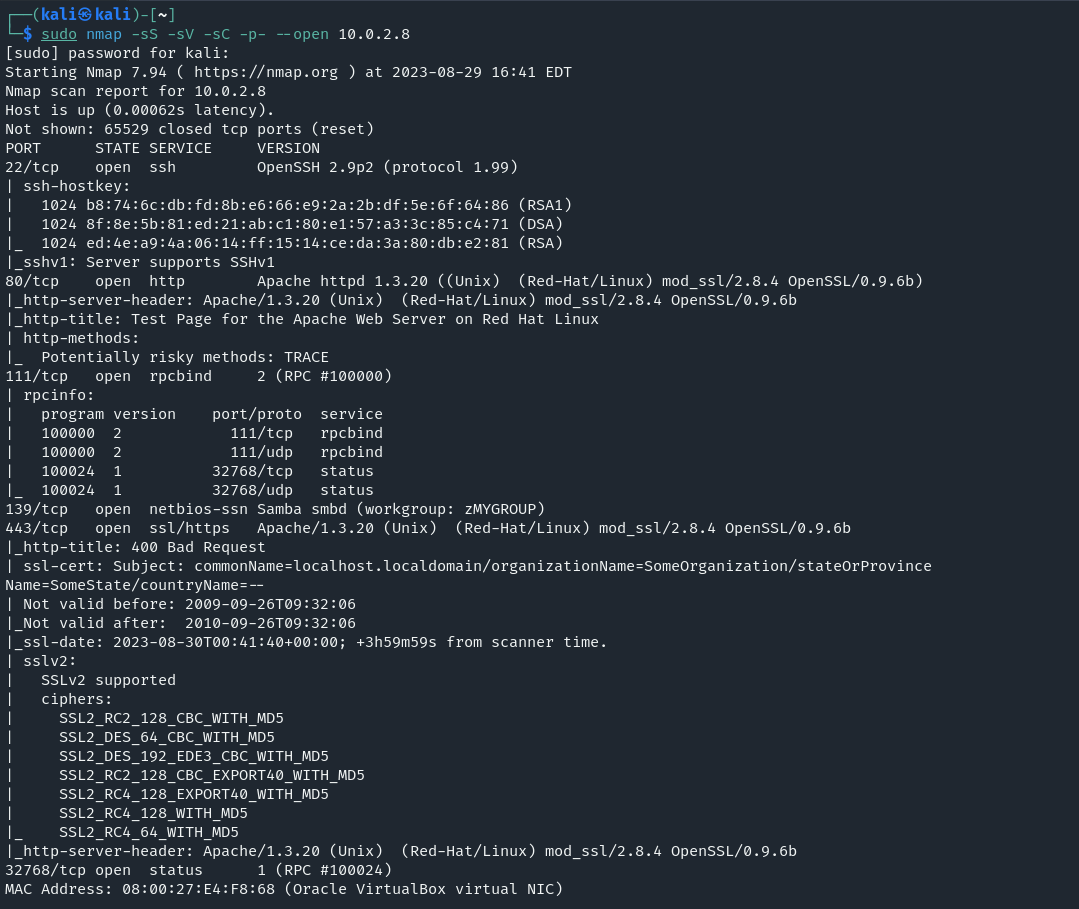
There’s a lot to digest from the nmap scan results, we’ll take it step by step, as probably there are multiple ways to compromise this machine.
HTTP/S Enumeration.
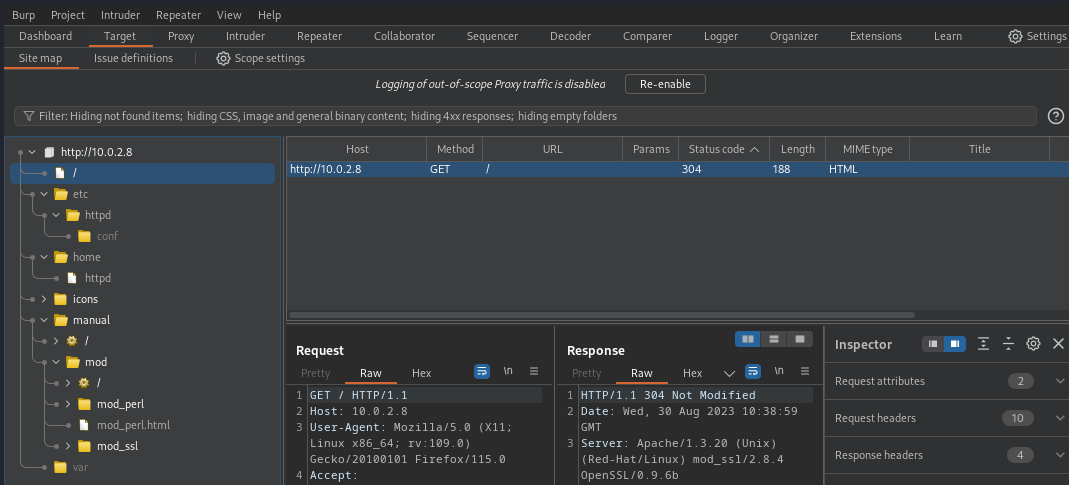
Looking at the website itself and viewing the source, we can determine that the server is Apache 1.3.20 and OS is RHEL, revealling a bit more on the sitemap if we use Burp Suite.
Let’s also use an nmap script and see if anything interesting comes up.
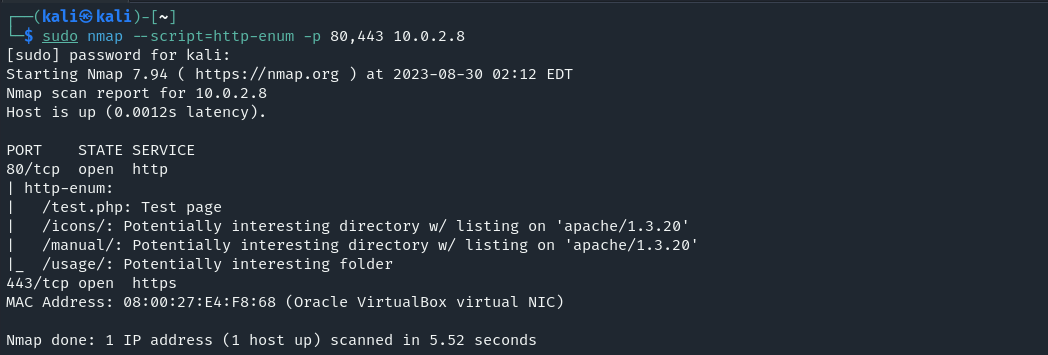
We see some directories discovered. Under /manual/ there’s a “mod” directory containing additional stuff which i do not know what that is yet, i’ll probably return to it later.
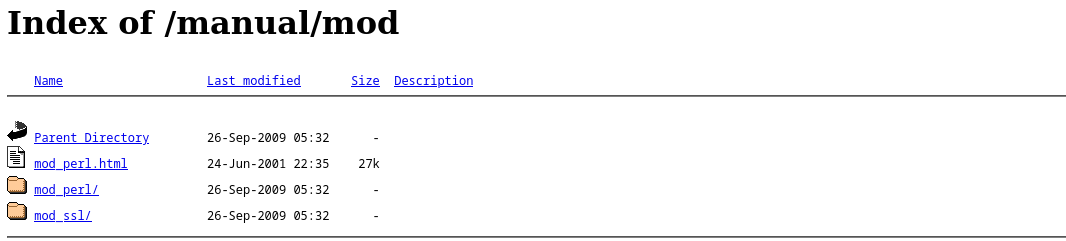
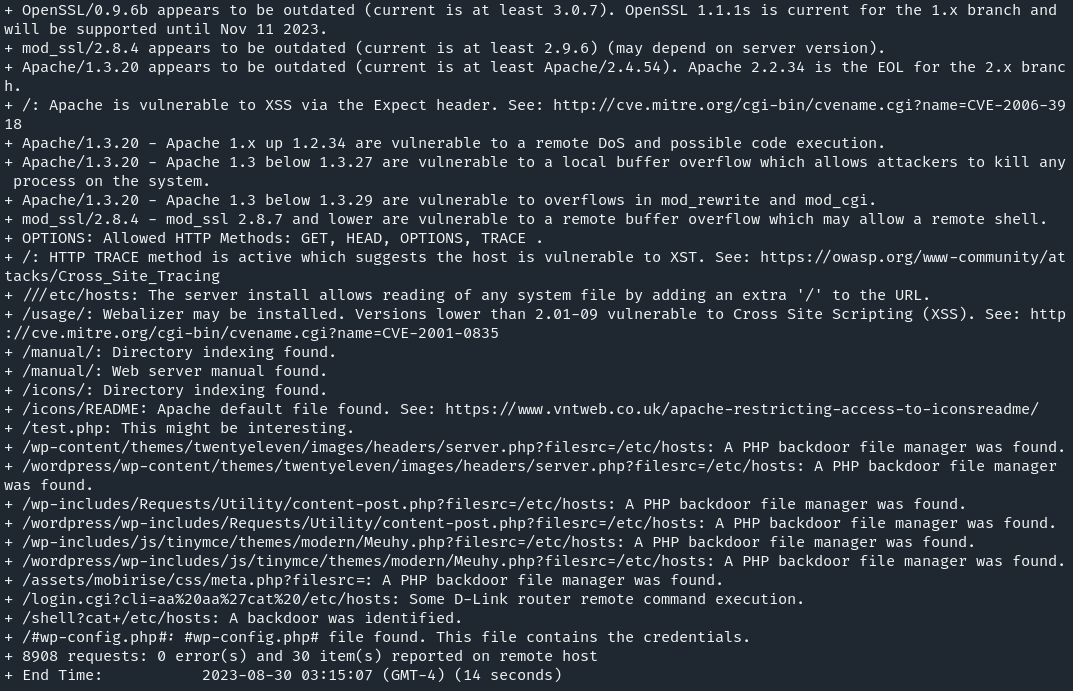
Additionally to what Burp discovered, we have /usage/ directory, containing a dashboard indicating Usage Statistics. The dashboard is generated with a Webalizer version which is likely vulnerable to buffer overflow - found many google results pointing to BOF and will dig this out later. For now i would use some additional resources and keep enumerating.
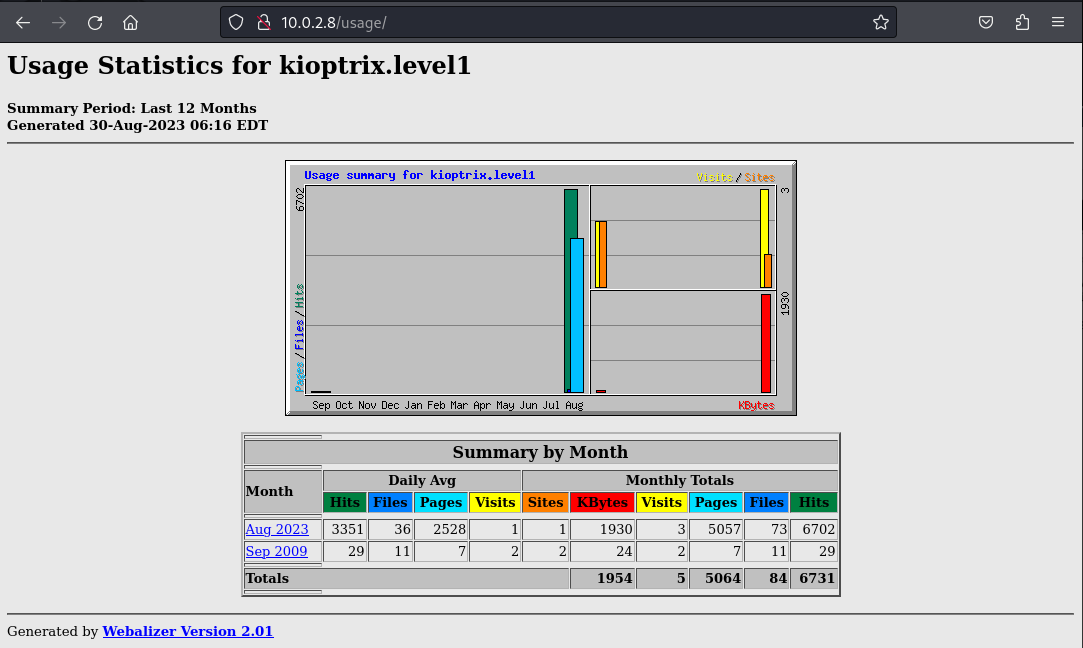
A Nikto scan reveals a considerable number of potential vulnerabilities and vectors for gaining an initial foothold on the machine(outdated Apache, vulnerable mod_ssl, backdors, hidden content, etc.)
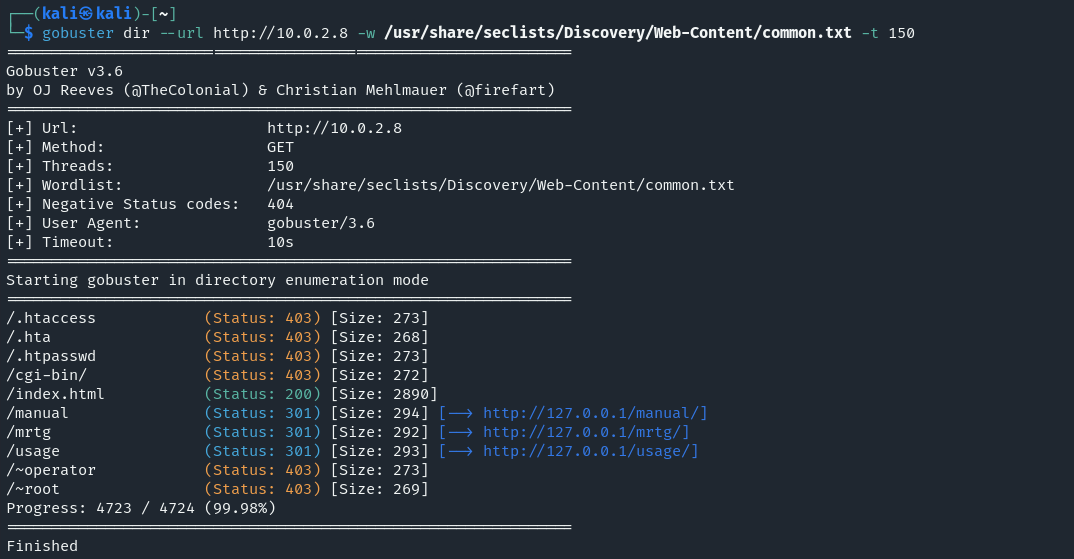
Executing a Gobuster scan for hidden directories we find some additional locations which might be interesting.
Work in progress…




